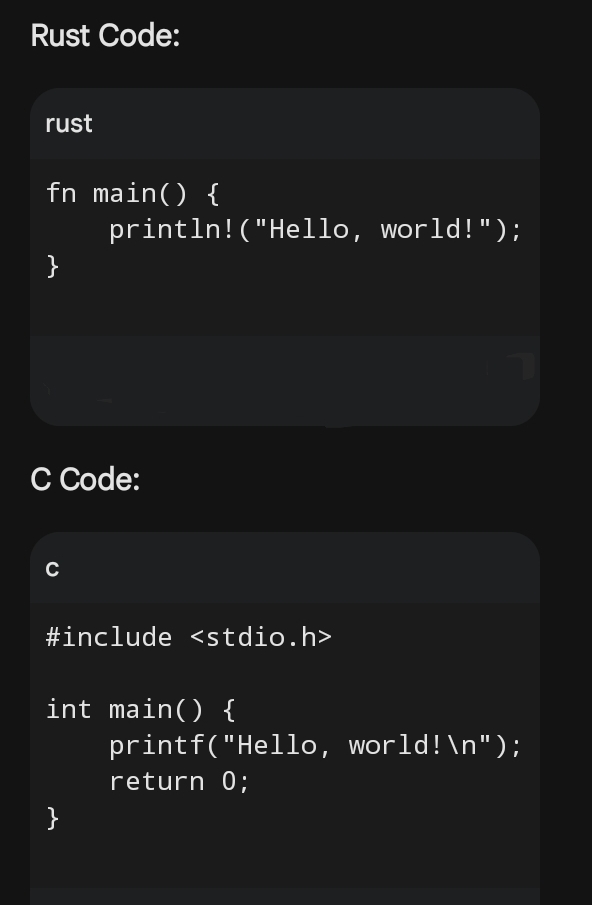
Rust vs C: The Real Differences and Why You Should Choose One Over the Other
Introduction to Rust and C Rust and C are two prominent programming languages that occupy significant places in the software development landscape. C, developed in the early 1970s by Dennis Ritchie at Bell Labs, has shaped many modern programming languages and systems. Its influence extends to the development of operating systems, embedded systems, and even … Read moreRust vs C: The Real Differences and Why You Should Choose One Over the Other