Introduction to Quantum Computing
Quantum computing is an advanced computational paradigm that revolutionizes the traditional frameworks established through classical computing. At its core, quantum computing leverages the principles of quantum mechanics, which enable computers to perform certain calculations significantly faster than their classical counterparts. Key principles that underpin quantum computing include superposition and entanglement.
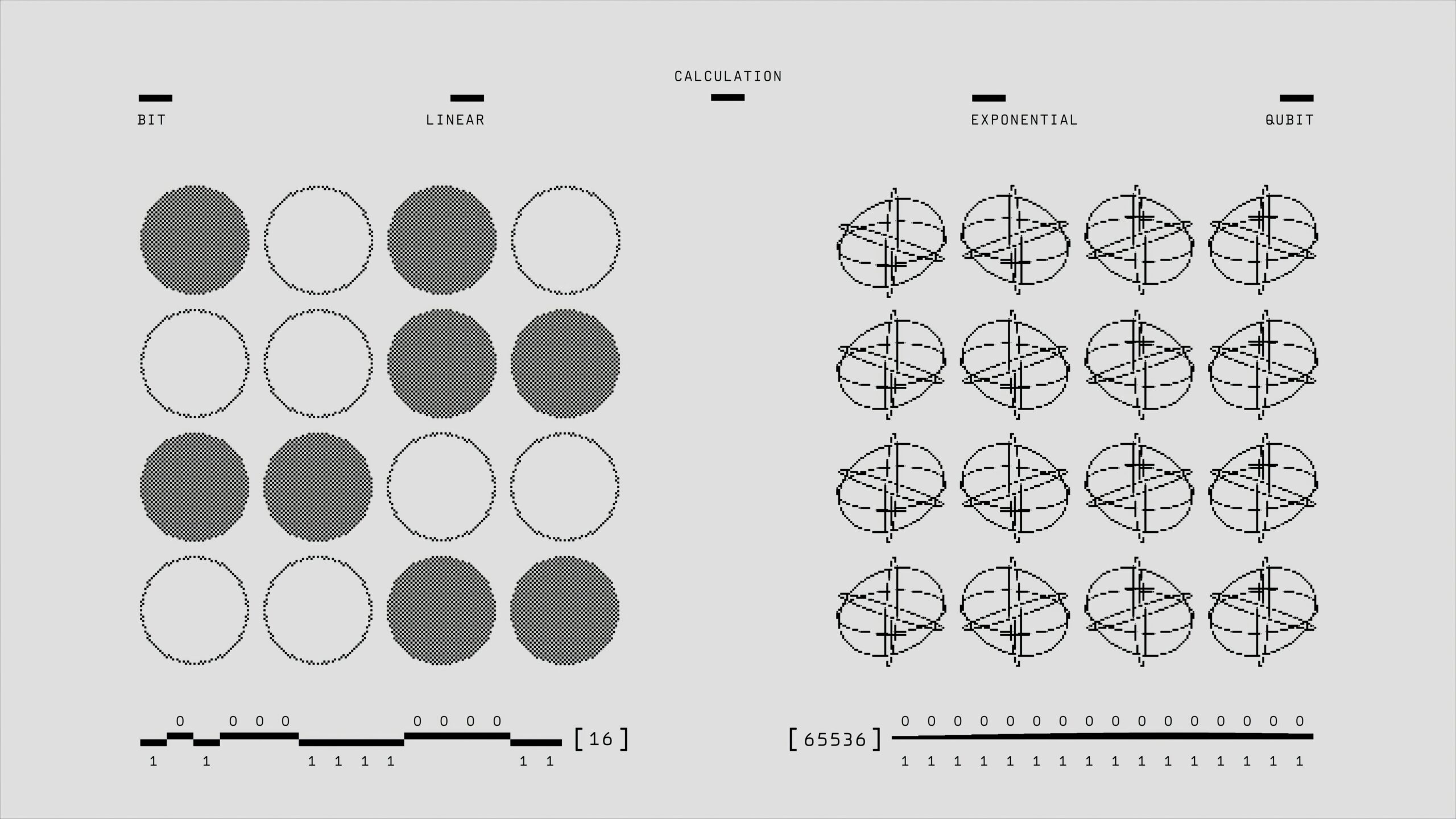
Superposition allows a quantum bit, or qubit, to exist in multiple states simultaneously, as opposed to a classical bit, which can only be in a state of 0 or 1. This capability exponentially increases the computational power of quantum systems. For instance, while classical computers process strings of bits in sequential fashion, a quantum computer can evaluate numerous possibilities at once due to superposition. This phenomenon opens up unprecedented potentials for solving complex problems in fields ranging from cryptography to materials science.
Entanglement, another fundamental concept of quantum mechanics, plays a vital role in quantum computing. It describes a unique correlation between qubits whereby the state of one qubit can instantaneously influence the state of another, regardless of the distance separating them. This characteristic enables quantum computers to perform intricate calculations that are not feasible for classical computers, thereby providing a significant edge in processing power.
Moreover, the stark contrast between classical and quantum computing extends beyond just their operational principles. Classical computers are bound by limitations in processing speed and data handling, constraints that become increasingly problematic as data complexity escalates. In contrast, quantum computers offer a paradigm shift, essentially redefining mathematical problems that were once deemed insurmountable. As research and development in quantum technology advance, understanding these fundamental principles is crucial for grasping the implications quantum computing holds for various sectors, particularly in the realm of cybersecurity.
Current Landscape of Cybersecurity
The realm of cybersecurity is continually evolving as organizations face a myriad of threats and challenges in the digital landscape. In today’s interconnected world, data breaches, ransomware attacks, and phishing schemes are prevalent, emphasizing the need for robust cybersecurity measures. Organizations of all sizes deploy various strategies to protect sensitive information, safeguard their digital assets, and maintain the trust of their stakeholders. Traditional cybersecurity measures, including firewalls, intrusion detection systems, and antivirus software, form the first line of defense. However, the effectiveness of these systems is being increasingly tested by sophisticated cybercriminals who leverage advanced techniques to bypass defenses.
One of the most critical components of cybersecurity is encryption, which is used to safeguard data in transit and at rest. Currently, symmetric and asymmetric encryption methods are the standard approaches. However, these traditional encryption techniques are not impervious to vulnerabilities. For instance, advancements in computational power and the emergence of quantum computing present new challenges that could render current encryption methods obsolete. The computational capabilities of quantum computers could potentially break widely used encryption algorithms, such as RSA and ECC, by efficiently solving complex mathematical problems that underpin their security.
In addition to this, organizations are also grappling with human factors that contribute to security vulnerabilities. Social engineering tactics, such as phishing, exploit human psychology and undermine even the most secure systems. As these threats become more prevalent, businesses must adapt their cybersecurity strategies and training to counteract them effectively.
Despite these challenges, organizations remain optimistic about improving their overall cybersecurity posture. By investing in more advanced technologies and training staff to recognize potential threats, companies can enhance their resilience against cyberattacks. As we explore further, it will become evident how quantum computing can both threaten and potentially fortify these cybersecurity measures in the future.
How Quantum Computing Works
Quantum computing represents a significant departure from classical computing, primarily due to its fundamental unit of information, the quantum bit or qubit. Unlike a classical bit that exists in a state of either 0 or 1, a qubit can exist in multiple states simultaneously, thanks to a phenomenon known as superposition. This unique characteristic allows quantum processors to process vast amounts of data concurrently, vastly increasing computational capability for specific tasks.
In addition to superposition, qubits leverage another principle of quantum mechanics known as entanglement. When two or more qubits become entangled, the state of one qubit becomes dependent on the state of the other(s), regardless of the distance between them. This interconnectedness could potentially enhance communication efficiency and security in cybersecurity applications. By exploiting entanglement, quantum computers can solve complex problems much quicker than their classical counterparts.
Quantum gates play a crucial role in quantum computing as they manipulate qubits in specific ways to perform calculations. These gates are analogous to classical logic gates but operate on the probabilistic nature of qubits, allowing them to perform operations that manipulate qubit states. Quantum algorithms, such as Shor’s algorithm for factoring integers and Grover’s algorithm for database searching, showcase the potential of quantum computing to outperform classical algorithms in specific scenarios. For instance, Shor’s algorithm poses a significant threat to conventional cryptographic methods, as it can efficiently break widely used encryption protocols.
Understanding these mechanisms of quantum computing is essential for appreciating its implications for cybersecurity. As quantum technology develops, it presents both potential threats to current security infrastructure and opportunities for developing new, quantum-resistant security measures. Grasping the principles of qubits, gates, and algorithms will prepare organizations for the rapidly evolving landscape of cybersecurity in the quantum computing era.
Potential Threats Posed by Quantum Computing
As quantum computing technology advances, it presents unique challenges and potential threats to the field of cybersecurity. One of the most notable risks involves the ability of quantum computers to break existing encryption protocols that are foundational to secure communications. At the forefront of this potential threat is Shor’s algorithm, a quantum algorithm developed for integer factorization. This algorithm can exponentially speed up the process of factoring large numbers, which directly undermines the security of widely used cryptographic systems such as RSA (Rivest-Shamir-Adleman) and ECC (Elliptic Curve Cryptography).
RSA encryption, which relies on the difficulty of factoring large prime numbers, is particularly vulnerable. Classical computers would take an impractically long time to factor these numbers, providing a level of security. However, a sufficiently powerful quantum computer exploiting Shor’s algorithm could factor these numbers in polynomial time, rendering RSA encryption obsolete. As a result, any data secured using RSA could potentially be exposed to interception and decryption by malicious actors equipped with quantum computing capabilities.
Similarly, ECC, which is favored for its efficiency and strength in smaller key sizes, is also susceptible to the advantages offered by quantum algorithms. Quantum attacks on ECC could enable attackers to derive private keys from public keys, compromising the security of both web traffic and sensitive data exchanges that currently rely on this encryption method.
Given these vulnerabilities, organizations must proactively consider the implications of quantum computing on their cybersecurity strategies. The transition to quantum-resistant algorithms, such as lattice-based or hash-based cryptography, is essential to maintain the integrity and confidentiality of data. As the landscape of computing evolves, addressing these potential threats must be an integral part of preparing for a future shaped by quantum technologies.
Quantum Computing and Data Privacy
As advancements in quantum computing continue to unfold, they carry profound implications for data privacy across various sectors. Quantum computers leverage quantum bits, or qubits, which enable them to process information at a speed unattainable by classical computers. This unprecedented computational power raises substantial concerns, particularly regarding the security of encrypted data systems that currently protect sensitive information.
Traditional cryptographic methods, such as RSA and ECC, form the backbone of data security on the internet today. However, quantum algorithms, notably Shor’s algorithm, pose a significant threat as they can factor large numbers efficiently, rendering these encryption techniques vulnerable. If a sufficiently powerful quantum computer were to be developed, it could potentially decrypt sensitive information such as personal identifiers, financial records, and confidential communications within minutes, leading to vast implications for data privacy.
The potential for quantum computers to harvest and decode stored data presents a scenario where private information could become easily accessible to malicious actors. This poses a considerable risk not only for individuals but also for organizations that rely on the confidentiality of their data to maintain trust with clients and stakeholders. The breach of such information could result in devastating consequences, including financial loss, identity theft, and reputational damage.
In anticipation of these potential threats, a proactive approach is vital. Researchers and cybersecurity experts are exploring post-quantum cryptography solutions designed to withstand the capabilities of quantum computing. These new encryption standards are critical for safeguarding data privacy in an era where quantum computing becomes more prevalent. Organizations must begin transitioning to these resistant algorithms to ensure the integrity and confidentiality of their data moving forward.
Opportunities Presented by Quantum Computing
As the field of quantum computing advances, it brings forth a new paradigm that significantly influences various sectors, particularly cybersecurity. One of the most promising opportunities arising from quantum technologies is the enhancement of security protocols through innovative methods such as Quantum Key Distribution (QKD). QKD leverages the principles of quantum mechanics to create secure communication channels that are fundamentally different from traditional cryptographic techniques.
In traditional systems, data encryption relies on complex algorithms and computational difficulty to secure information. However, these systems are increasingly vulnerable to the rise of powerful classical and potential quantum computers that could break existing encryption methods. Quantum Key Distribution addresses this issue by using quantum bits (qubits) to establish a shared secret key between parties. The key feature of QKD is that it guarantees the detection of any eavesdropping attempts, as observing a quantum system inherently alters its state. This results in a robust security measure that is theoretically unbreakable if executed correctly.
Moreover, the integration of quantum techniques into cybersecurity frameworks paves the way for enhanced security protocols that can safeguard sensitive information against both known and emerging threats. Organizations can leverage advancements in quantum computing to develop new cryptographic algorithms that harness quantum phenomena, ensuring data integrity and confidentiality. This advancement not only increases security resilience but can also facilitate safe communication over insecure channels, thereby significantly improving the opportunities for secure transactions in a digital-first world.
Furthermore, quantum computing could lead to the creation of innovative security solutions adaptive to the evolving nature of cyber threats. By embracing such cutting-edge technologies, businesses and governments can prepare more effectively for potential vulnerabilities in their networks, thereby enhancing their overall cybersecurity infrastructure.
Post-Quantum Cryptography: An Overview
As the field of quantum computing evolves, the necessity for robust security measures becomes increasingly urgent. Quantum computers have the potential to break traditional cryptographic algorithms, which rely on the difficulty of problems such as integer factorization and discrete logarithms. In light of this impending threat, researchers and cybersecurity experts are investigating post-quantum cryptography (PQC). This area of study focuses on developing cryptographic systems that remain secure against quantum attacks.
Post-quantum cryptography encompasses various approaches, including lattice-based, code-based, multivariate polynomial, and hash-based cryptographic systems. Each of these methods offers unique advantages in terms of security and performance. For example, lattice-based cryptography is gaining traction due to its strong theoretical foundations and versatility for both encryption and digital signatures. By utilizing complex mathematical structures known as lattices, these systems can effectively withstand potential quantum computing threats.
The transition to post-quantum standards is not merely a theoretical exercise; it is a critical step towards safeguarding sensitive information. Organizations must begin to evaluate their current cryptographic protocols and consider the implementation of PQC solutions. The National Institute of Standards and Technology (NIST) has been actively working on this front, recently announcing a shortlist of algorithms that have shown promise in providing security against quantum attacks. Adopting these new standards is essential to ensure data integrity and trust in digital communications.
While the field of post-quantum cryptography is still developing, its implications for the future of cybersecurity are profound. Preparation for potential quantum threats requires ongoing research, collaboration, and a proactive approach to adopting secure algorithms. Organizations must remain informed about advancements in PQC to effectively mitigate risks associated with quantum computing.
Major Players in Quantum Cybersecurity
The landscape of quantum cybersecurity is currently shaped by a variety of key organizations and researchers, both in the private sector and within governmental initiatives. These stakeholders play pivotal roles in developing advanced secure systems, specifically designed to counteract the potential threats that quantum computing poses to traditional cybersecurity frameworks.
Among the notable private-sector leaders is IBM, which has been at the forefront of quantum computing research. IBM’s quantum processors are integrated with tools aimed at enhancing cybersecurity measures, such as Quantum Key Distribution (QKD). Their Quantum Safe initiative illustrates a commitment to developing algorithms that can withstand quantum attacks, thereby promoting a secure future in digital communications.
Google, another major player, has made significant contributions through its Quantum AI lab. By focusing on harnessing quantum computing for various applications, Google aims to enhance encryption techniques and promote robust cybersecurity measures. Their research on post-quantum cryptography seeks to create algorithms resilient against the capabilities introduced by quantum systems.
In the realm of governmental efforts, the National Institute of Standards and Technology (NIST) in the United States is a leading authority. NIST is currently working on standardizing post-quantum cryptographic algorithms, which is essential for building a resilient cybersecurity framework capable of withstanding the advancements in quantum computing.
Additionally, leading academic institutions play a vital role in this field. Universities such as MIT and Stanford are conducting research focused on quantum computing and its implications for cybersecurity. Their academic endeavors contribute significantly to our understanding of how to create secure systems that can protect sensitive information in a quantum future.
These organizations, both privately owned and government-run, represent the collective efforts required to navigate the complexities of quantum cybersecurity. By advancing technology and research, they are not only preparing for potential threats but also unveiling new opportunities in the realm of secure communications.
Global Initiatives on Quantum Standards
The emergence of quantum computing has prompted significant international dialogue regarding the establishment of standards that ensure cybersecurity in this new technological arena. Recognizing the potential risks and opportunities presented by quantum technologies, nations and institutions are collaborating to create frameworks that will safeguard sensitive information in a post-quantum world. Organizations such as the International Organization for Standardization (ISO) and the National Institute of Standards and Technology (NIST) have taken pivotal roles in developing guidelines specifically aimed at quantum security.
One of the principal objectives of these global initiatives is to develop standards for quantum-resistant cryptography. As quantum computers gain proficiency, traditional encryption methods become increasingly vulnerable to attacks that could potentially compromise the integrity of secure communications. Collaborative efforts among countries have led to discussions about benchmarking cryptographic algorithms that will withstand quantum threats, thus ensuring data protection remains robust in the quantum era.
This collaborative approach transcends borders, with countries pooling their resources and expertise to address the implications of quantum computing on cybersecurity. For instance, nations such as the United States, the European Union, and China are actively participating in joint research initiatives and forums aimed at devising effective quantum security measures. Additionally, partnerships with academia and the private sector foster innovation and quick adaptation of security protocols as technologies evolve.
Moreover, international dialogue is crucial for harmonizing standards that can be uniformly accepted across borders, facilitating cooperation in cybersecurity. As states recognize the shared nature of cyber threats, developing comprehensive quantum standards becomes essential for creating a secure global digital environment. Moving forward, these initiatives will play a significant role in shaping the future of cybersecurity, ultimately safeguarding critical infrastructures against the unpredictable challenges posed by quantum computing.
Risk Management and Compliance in Quantum Era
The advent of quantum computing has significant implications for risk management and compliance frameworks within organizations. As quantum technology continues to evolve, businesses must adapt their risk management strategies to address the unique challenges posed by quantum threats. Traditional risk assessment methods may no longer suffice, as quantum computers are capable of executing complex computations at unprecedented speeds, potentially compromising existing encryption methods used to safeguard sensitive data.
Organizations should proactively reevaluate their risk management frameworks by incorporating quantum-related risks into their existing processes. This involves understanding the potential vulnerabilities quantum computing may introduce and identifying critical assets that require immediate protection. By conducting comprehensive risk assessments, businesses can develop a clearer picture of their exposure and determine the appropriate measures needed to mitigate these risks, including transitioning to quantum-resistant cryptographic standards.
Compliance with emerging quantum standards is vital for maintaining regulatory obligations and ensuring that organizations are positioned to defend against cyber threats. Businesses should stay abreast of developments in both national and international quantum cybersecurity regulations, engaging with industry stakeholders to understand best practices and anticipated compliance requirements. Establishing partnerships with quantum technology experts can also provide organizations with insights into how to fortify their cybersecurity protocols effectively.
Furthermore, training and awareness programs centered around quantum computing should be implemented to equip employees with the knowledge to identify and respond to potential quantum threats. Employees must understand the significance of data protection in a quantum context, fostering a culture of security that prioritizes compliance and risk management. By embracing a proactive and informed approach, businesses can navigate the complexities introduced by quantum computing, ensuring they remain resilient against potential cybersecurity challenges.
Challenges in Adopting Post-Quantum Solutions
The transition to post-quantum cryptography poses several challenges for organizations looking to enhance their cybersecurity frameworks. One of the primary hurdles is the technical complexity associated with implementing new cryptographic algorithms designed to withstand quantum attacks. Unlike classical systems, post-quantum systems require a thorough understanding of not just the new technologies but also their integration with existing infrastructure. This complexity can create significant barriers to adoption as organizations must allocate substantial time and resources to train personnel and refine existing processes.
Moreover, the cost implications of adopting post-quantum solutions can discourage organizations, especially small to medium enterprises (SMEs). The financial burden encompasses not only the expenses related to new software and hardware but also those tied to the necessary workforce training and potential system overhauls. As organizations evaluate their cybersecurity budgets, the added costs of transitioning to post-quantum cryptography may appear unwarranted, particularly when the perceived immediate threat from quantum computing remains uncertain. This makes justifying the upfront investment a complex undertaking.
Furthermore, there is a pressing need for widespread industry education regarding post-quantum cryptography. Many organizations lack the awareness and understanding of the implications posed by quantum computing and the importance of adopting resilient cryptographic solutions. Without comprehensive educational programs that address these knowledge gaps, organizations may continue to operate under outdated systems that are vulnerable to future quantum threats. This uncertainty underlines the necessity for more resources dedicated to industry-wide education initiatives to facilitate the transition to secure post-quantum solutions, ensuring that both stakeholders and IT professionals are properly informed.
Preparing Your Infrastructure for Quantum Threats
As organizations increasingly embrace digital transformation, the emergence of quantum computing presents both opportunities and challenges. To mitigate the potential threats posed by quantum capabilities, it is imperative for organizations to proactively prepare their IT infrastructure. The following actionable steps can serve as a guide for achieving quantum readiness.
First, organizations should conduct a comprehensive risk assessment to identify sensitive data or systems that would be vulnerable to quantum attacks. This assessment should prioritize data encryption methods currently in use, as quantum computers can potentially crack traditional encryption algorithms. By evaluating the robustness of existing encryption protocols, organizations can determine which areas require immediate attention.
Next, organizations should consider transitioning to post-quantum cryptography (PQC). This emerging field focuses on developing encryption algorithms resistant to quantum attacks. Engaging with cryptographic experts can assist organizations in selecting and implementing suitable PQC algorithms that can safeguard their data from future quantum threats. Early adoption allows for ample time to test and integrate these new protocols into existing systems before quantum capabilities become mainstream.
Additionally, it’s crucial to strengthen the overall IT security framework. Organizations should enhance their security policies, implement multi-factor authentication, and increase employee training on cybersecurity practices. Fostering a culture of security awareness reduces the likelihood of successful attacks, complementing the transition to quantum-resistant technologies.
Finally, collaboration is key. Organizations should establish partnerships with industry experts and participate in information-sharing networks. Engaging in collaborative efforts allows entities to stay abreast of advancements in quantum computing, as well as share insights and strategies for building quantum-resilient infrastructures.
In conclusion, preparing the IT infrastructure for potential quantum threats is essential for safeguarding organizational data and ensuring business continuity in an evolving technological landscape. By adopting a proactive approach, organizations can bolster their defenses while positioning themselves to harness the benefits of quantum advancements.
Case Studies: Organizations Leading the Way
Various organizations are actively engaging in the development and implementation of quantum-resistant measures to bolster their cybersecurity frameworks. One notable example is the European Union Agency for Cybersecurity (ENISA), which has undertaken initiatives to identify and mitigate risks associated with quantum computing. ENISA collaborates with technological partners to create comprehensive guidelines that facilitate the adoption of quantum-resistant cryptographic algorithms. Such initiatives are aimed at improving the overall cybersecurity landscape within Europe and ensuring that digital infrastructure is protected from future quantum threats.
Another prominent case is that of Google, which has invested significantly in quantum computing research. The company’s Quantum Artificial Intelligence Lab not only advances quantum computational capabilities but also addresses cybersecurity vulnerabilities that may arise from quantum developments. Google has proactively explored quantum key distribution (QKD), which offers a method of secure communication that is theoretically impervious to eavesdropping by quantum computers. By investing in quantum cybersecurity technologies, Google is setting a precedent for other tech companies while safeguarding sensitive information against future risks.
Additionally, the National Institute of Standards and Technology (NIST) is playing a crucial role in leading global efforts to standardize post-quantum cryptography. NIST’s initiative is essential in guiding organizations through best practices for adapting their current encryption systems. Through ongoing evaluations and workshops, NIST aids in the identification of quantum-resistant algorithms that can be seamlessly integrated into existing platforms, thus enabling organizations to transition more effectively in preparation for the quantum era.
These case studies illustrate the proactive measures being implemented by organizations at the forefront of cybersecurity. By integrating quantum-resistant technologies and fostering collaboration across sectors, these entities contribute to a robust framework that addresses emerging cybersecurity threats posed by quantum computing.
The Role of Government in Quantum Cybersecurity
The evolving landscape of quantum computing presents significant implications for cybersecurity, making the role of government crucial in mitigating potential risks and harnessing opportunities. Government entities worldwide are increasingly recognizing the importance of establishing robust frameworks that can guide the integration of quantum technologies into national and international security protocols. Central to this effort is funding—governments are directing investment towards research and development initiatives aimed at exploring quantum cryptography and developing secure communication infrastructures. These investments are essential to stay ahead of emerging quantum threats that could exploit existing vulnerabilities in classical encryption methods.
Moreover, government regulations play a pivotal role in shaping the quantum cybersecurity framework. Policymakers need to establish guidelines that ensure the security of sensitive information against potential quantum attacks. This may involve updating existing laws and regulations to accommodate for advancements in quantum technology and its capabilities. It is imperative that regulatory bodies collaborate with scientists and industry experts to develop standards that are both comprehensive and flexible, allowing for the swift evolution of practices as the quantum landscape changes.
In addition to funding and regulation, the promotion of partnerships between the public and private sectors is vital for enhancing quantum cybersecurity. Governments can provide a platform for collaboration by facilitating knowledge sharing and resource allocation among academic institutions, technology firms, and cybersecurity experts. Establishing public-private partnerships ensures that critical insights and innovations are leveraged effectively, fostering a collective approach to developing quantum-resistant solutions. As quantum computing continues to advance, a cohesive strategy involving both government and private sector stakeholders will be essential in addressing the complex challenges and opportunities that arise in the realm of quantum cybersecurity.
Public Perception and Awareness of Quantum Risks
The burgeoning field of quantum computing has generated significant interest, yet public perception remains varied and, at times, limited. Many individuals are unfamiliar with the fundamental principles of quantum mechanics and how they relate to emerging technologies. This lack of understanding extends to the implications quantum computing may have on cybersecurity, a critical component of modern digital infrastructure. As quantum technologies evolve, so too must the collective awareness of their potential risks and opportunities.
Efforts to bridge this knowledge gap have become increasingly important. Various organizations, academic institutions, and government bodies are actively working to promote education regarding quantum risks and benefits. These initiatives emphasize the need for both technical and non-technical audiences to grasp the basic concepts of quantum computing. This understanding is vital, as quantum computers possess the potential to undermine traditional encryption methods currently used to protect sensitive data. Consequently, a proactive approach is essential to ensure that the public remains informed about how such advancements may impact their personal information and organizational security.
Furthermore, engaging the media in discussions about quantum computing can play a critical role in shaping public perception. Articles, podcasts, and documentaries can demystify complex topics and highlight the dual nature of quantum technologies: while they present opportunities for advancements in various fields, they also pose significant cybersecurity challenges. The narrative surrounding quantum risks must strike a balance, leveraging both excitement and caution to prepare society for the impending changes. Enhanced public discourse on this matter will be crucial in cultivating an informed populace that can effectively respond to the challenges presented by quantum computing, thereby improving overall cybersecurity resilience.
Future Outlook: The Next Decade in Quantum Cybersecurity
The next decade promises to be transformative for quantum cybersecurity as advancements in quantum computing reach new heights. With the advent of increasingly powerful quantum computers, the potential for these machines to disrupt existing encryption methods is a pressing concern. Predictions suggest that by 2030, quantum computers may be capable of breaking widely-used cryptographic protocols, necessitating a proactive approach to cybersecurity. As such, organizations must prioritize the development and implementation of quantum-resistant algorithms and strategies to shield sensitive data from emerging threats.
Regulatory changes will also play a crucial role in shaping the landscape of quantum cybersecurity. Governments and regulatory bodies are becoming more aware of the vulnerabilities posed by quantum computing. As a response, they are likely to introduce frameworks aimed at fortifying national cybersecurity infrastructures. These regulations may mandate the adoption of quantum-safe cryptographic standards, compelling businesses to innovate and adapt in order to remain compliant. Consequently, organizations that position themselves as leaders in quantum cybersecurity will gain a competitive advantage in the market.
Furthermore, the emergence of new threats in the cyber landscape will warrant a reevaluation of current security measures. As quantum technologies evolve, cybercriminals may exploit these advancements to create sophisticated attack vectors. Organizations must, therefore, foster a culture of continuous risk assessment and improvement, ensuring their defenses can thwart both quantum and classical threats. Collaborating with experts in the field and investing in research will be imperative for developing robust security solutions.
In conclusion, the next decade in quantum cybersecurity will be characterized by rapid technological advancements, regulatory reforms, and a shifting threat landscape. Organizations must remain vigilant and adaptable to navigate these changes effectively, ensuring their cybersecurity posture evolves in tandem with advancements in quantum computing.
Conclusion: The Need for Vigilance and Innovation
The rapid evolution of quantum computing poses unprecedented challenges and opportunities within the realm of cybersecurity. As previously discussed, the advent of quantum technology introduces significant risks to traditional encryption methods, highlighting an urgent need for vigilance among security professionals and organizations alike. The potential for quantum computers to effortlessly break through conventional cryptographic systems necessitates immediate action to safeguard sensitive information and maintain the integrity of digital communications.
In response to these emerging threats, innovation becomes essential. The development of quantum-resistant algorithms and new encryption techniques is crucial in addressing the vulnerabilities that quantum computing introduces. Research and investment in post-quantum cryptography are vital to creating robust security measures capable of withstanding the challenges posed by advanced quantum systems. Additionally, organizations must stay informed about ongoing advancements in quantum technology to preemptively adapt their security protocols.
Furthermore, proactive collaboration between researchers, policymakers, and industry leaders is critical to establishing comprehensive frameworks that anticipate future risks. By engaging in knowledge sharing and fostering a culture of continuous improvement, stakeholders can more effectively navigate the complexities associated with quantum advancements. Educating teams on the implications of quantum computing on cybersecurity will also empower them to implement informed strategies and foster a resilient digital landscape.
The integration of awareness and innovation is fundamental to navigating the potential challenges brought about by quantum computing. In embracing a forward-thinking mindset, organizations can better prepare for the evolving technological landscape, ensuring not only their security but also the trust of their clients and partners in an increasingly complex digital environment. As the curtain rises on the quantum era, the onus is on us to remain vigilant and innovative as we adapt to its profound impact on cybersecurity.
Further Reading and Resources
For those interested in delving deeper into the intricate relationship between quantum computing and cybersecurity, a variety of resources are available that provide insightful analysis, research, and commentary on this evolving field. One highly recommended book is “Quantum Computing for Computer Scientists” by Noson S. Yanofsky and Mirco A. Mannucci, which serves as a robust introduction to the principles of quantum computing and its implications for information security. Readers will find that the authors articulate complex concepts with clarity, making the subject accessible to both novices and seasoned professionals.
In addition to foundational texts, academic papers shed light on specific aspects of quantum threats and defenses. Notably, “Quantum Computing and Cryptography” by R. P. Feynman offers a scholarly examination of how quantum algorithms could potentially undermine current encryption practices. This paper underscores the urgency for cybersecurity professionals to adapt to the impending challenges presented by quantum technologies.
Online resources also play a pivotal role in keeping practitioners up-to-date. The National Institute of Standards and Technology (NIST) frequently publishes reports and guidelines focusing on quantum-resistant cryptography. Their ongoing initiatives aim to prepare organizations for the eventual transition to quantum-safe algorithms, ensuring that sensitive data remains protected against future threats.
For more hands-on learning, tutorials and webinars available through platforms like Coursera and edX provide practical insights into quantum programming and its potential applications in cybersecurity. These interactive courses offer an engaging way to explore the technological advancements that are reshaping the cybersecurity landscape.
Finally, staying informed through dedicated forums and online communities such as Quantum Computing Stack Exchange allows for sharing ideas and strategies among peers. Such collaborative discourse enhances understanding and fosters innovative approaches to address the challenges that quantum computing presents to cybersecurity.